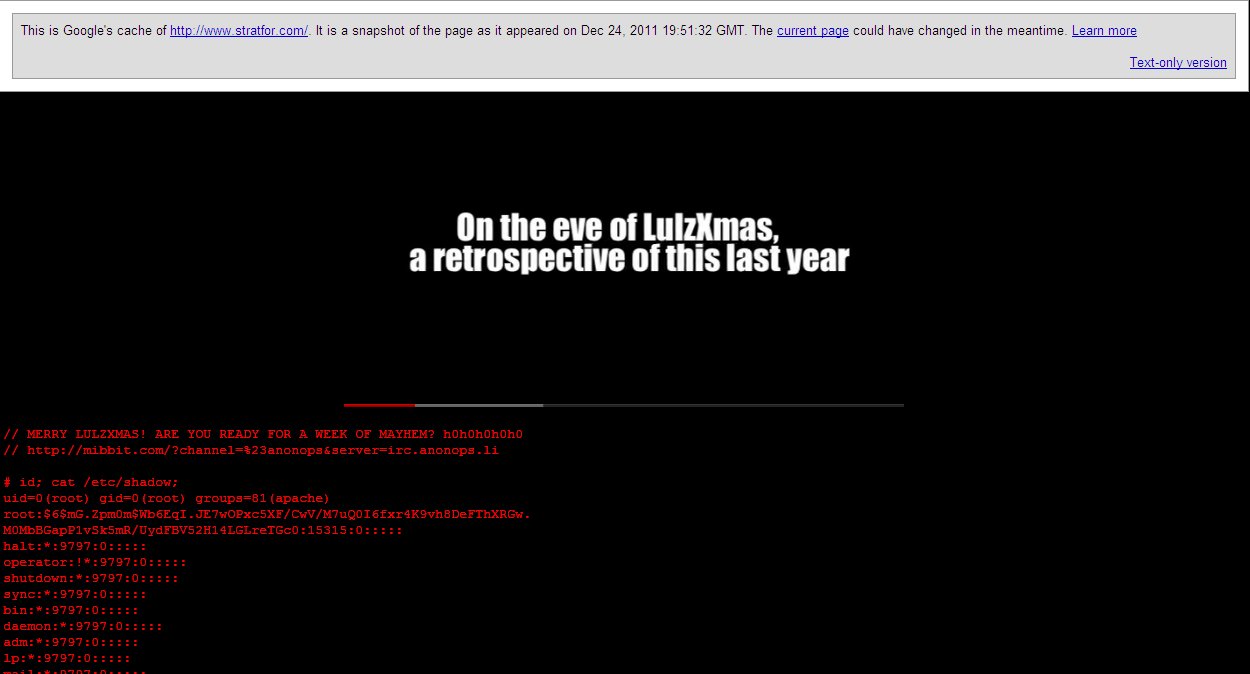
The website of intelligence firm Stratfor Research
appears to have been defaced and then DOSed (suffered a denial-of-service attack) by attackers.
The message traffic (below) -- if accurate -- portrays a defiant IT manager offering a, eh, perhaps
unwise challenge.
The Google cache recorded some of the content including shadow files and other sensitive info apparently rooted from Stratfor's servers. I've tactfully redacted some of the more sensitive info.
// OH STRATFOR. IF YOU ONLY KNEW WHAT ALL IS ABOUT TO GO DOWN.
// 'BUT WAIT', YOU ASK. 'IS THIS IT?' 0H N0, WE GOT MORE IN STORE...
// BUT FOR NOW, SOME INSPIRING WORDS OF WISDOM FROM IT MANAGER FRANK GINAC:
 "You do realize how preposterous it is to suggest that stratfor simply
"You do realize how preposterous it is to suggest that stratfor simply
shutdown completely for 2 days, right? The plan that you've attached paints a
gloom and doom picture claiming no chance that such a move will succeed. Does
that really seem a rationale conclusion?"
// YOU DONT EVEN KNOW THE EXTENT OF THE GLOOM AND DOOM WE HAVE PLANNED, FRANK

"Attended the TakeDownCon security conference. Focus of the conference was on
wireless and mobile security. No vendors pushing product or service at this
conference. Instead, great presentations by renowned white hat hackers (good
hackers) and security experts. Bottom line is that no mobile platform is
secure, including the Blackberry, but there are best practices that minimize
the risk of their use within the enterprise. We will be incorporating these
best practices in our operation over the coming months."
// INCORPORATING PRACTICES FROM "GOOD WHITE HAT HACKERS"? HOW'D THAT WORK OUT?
"It blew my mind to discover that our email server backups are being stored on
the same physical server. I'm affectionately referring to these little
discoveries as 'Mooney turds'."
// SO SAD WE RM'D YOUR MAIL SERVER AND ALL BACKUPS, FRANK
 "Most if not all of us use professional and social networking sites like
"Most if not all of us use professional and social networking sites like
LinkedIn and Facebook. All offer levels of privacy ranging from wide open
where everyone can see your profile, activities, and posts to closed allowing
only your immediate connections (or friends) access. As a private intelligence
company we must all take extra care to protect our personal information from
those who would use that information to exploit us personally or
professionally. Although we don't have hard and fast rules on how to set your
privacy settings nor do we restrict use of such sites, I suggest that you
temper your need to share with prudence and consider the business that we are
in. It's also important to check your privacy settings regularly to ensure
that the sites you use haven't changed the meaning or scope of privacy
settings -- we've all heard or read the news regarding this practice at
Facebook. I suggest that you never include any information in your profile --
regardless of privacy setting -- that could be used to compromise your
identity. Specifically, never include: your birth date, your exact street
address (although this information can usually be found on the web quite
easily), your cell phone number, SSN or other government issued ID number
(that should be obvious), or any other information that someone could use to
compromise your identity if your account were compromised."
// EVEN WITH ALL THE BEST SECURITY PRACTICES LEARNED FROM THE "RENOWNED WHITE
// HAT HACKERS" WE STILL MANAGED TO STEAL ALL YOUR PERSONAL INFORMATION. UMAD?
Interesting, to say the least.
Update:
Cryptome:
Subject: Important Announcement from STRATFOR
Date: Sat, 24 Dec 2011 19:49:58 -0500
From: STRATFOR
Dear Stratfor Member,
We have learned that Stratfor's web site was hacked by an unauthorized party. As a result of this incident the operation of Stratfor's servers and email have been suspended.
We have reason to believe that the names of our corporate subscribers have been posed on other web sites. We are diligently investigating the extent to which subscriber information may have been obtained.
Stratfor and I take this incident very seriously. Stratfor's relationship with its members and, in particular, the confidentiality of their subscriber information, are very important to Stratfor and me. We are working closely with law enforcement in their investigation and will assist them with the identification of the individual(s) who are responsible.
Although we are still learning more and the law enforcement investigation is active and ongoing, we wanted to provide you with notice of this incident as quickly as possible. We will keep you updated regarding these matters.
Sincerely,
George Friedman
STRATFOR
221 W. 6th Street, Suite 400
Austin, TX 78701 US
Update II:
Police-Led Intelligence:
PLI is far more concerned about the state of the classified information provided by STRATFOR to the US Government... STRATFOR maintains separate classified and unclassified networks and information, and PLI understands that none of the STRATFOR data has been spared the attention of the hacking group. Of course, had STRATFOR placed any classified data on the server which we know has been hacked, they’d be in blatant violation of the laws of the US and of common sense, but it’s against the law why? Because it’s happened before.
If classified data has been compromised in the hack, it will create a larger impact – and response – than if it is unclassified commercial intel. In addition, Sabu, a leading member of the group, boasted on Twitter that... "Over 90,000 Credit cards from LEA, journalists, intelligence community and whitehats leaked and used for over a million dollars in donations..."
The AntiSec/LulzSec crowd, on the AnonymousIRC Twitter channel, has promised that this is the first of many attacks.
Google has pledged cash prizes totaling $1 million to people who successfully hack its Chrome browser at next week's CanSecWest security conference.





